Bypassing LastPass Mobile UUID Restrictions
First published: 2/19/11
LastPass is a fantastic password management tool. For most people, it dramatically increases password security by decoupling password complexity from the limits of human memory. Any person that is forced to remember all of their passwords will, inevitably, pick relatively simple passwords and reuse them. This situation is thrust upon us by the current state of identity on the internet, where each of us is forced to remember myriad usernames and passwords. Until identity engineers find a sane way to collapse our tens and hundreds of fractured logins, services such as LastPass act as convenient gatekeepers for the bulk our passwords, allowing a person to remember only one strong password. The rest of the passwords need not be remembered at all, and can therefore be complex and rotated frequently.
One of the features about LastPass that I was really excited about was the ability to use multi-factor authentication to protect my LastPass vault, particularly yubikeys. Yubikeys are USB dongles that generate one-time passwords. Any service can tie to a yubikey server, and authenticate that the OTP generated belongs to the correct yubikey. The use of a yubikey in addition to a traditional password provides two-factor authentication (something you have and something you know), as the yubikey OTP can not be replayed.
Yubikeys present a problem in the mobile space, however, as most mobile devices do not have USB ports, making it impossible to use a yubikey. The response of LastPass was to offer access restrictions based upon the "UUID" of a mobile device. Unfortunately, the "UUID" of a mobile device does not, unlike a yubikey, offer replay protection. This post demonstrates that the LastPass mobile UUID can easily be spoofed.
It turns out that the UUID used by LastPass to identify a mobile device, at least for GSM phones, is just the IMEI. This was an unfortunate choice, as the IMEI for a device is readily available. On an Android phone, for example, the IMEI can be retrieved from the setting menu. It can be found under Menu - Settings - About Phone - Status.

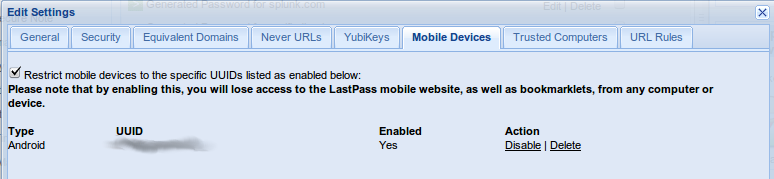
The IMEI number will show up in the LastPass settings as the UUID for the phone.
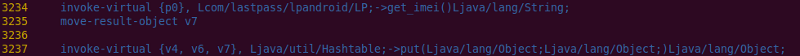
It turns out that it isn't terribly difficult to spoof the UUID that the lastpass application sends. Since the IMEI for a phone is relatively easy to obtain, the UUID restrictions that LastPass has put in place turn out to be relatively weak. Running the lastpass apk through apktool generates Smali code (decompiled Dalvik bytecode) that hasn't been obfuscated. Instructions for attaching Netbeans to DDMS for debugging Smali can be found on the apktool project page. Attaching the LastPass app to the Netbeans debugger through DDMS allows us to step through the code and see where the UUID is generated. As seen in the figure below, a call is made to the get_imei() method in LP.java, and the result is stored in the Smali variable v7, which will later be put in a Hashtable, along with the user's username and password.
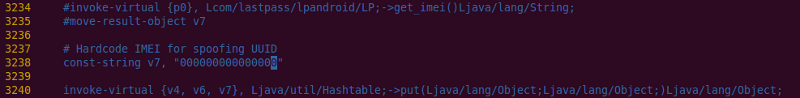
We can easily replace this code with the IMEI we want to spoof, as show below. Obviously, "000000000000000" would be replaced by a real IMEI. Simply rebuild the apk, sign it, and install it in an emulator or on a phone.
LastPass will accept the spoofed UUID (assuming the password is correct, of course) and allow the app to connect.